- Cyber Security Monitoring for all
- +44 20 3143 0308
- info@bluedogsec.com
Managed Detection and Response (MDR) Service
The highest level of protection made available for all sizes of organization
- While cybercrime is evolving every day,
- Cybersecurity is becoming more complex.
- While cybercriminals are growing in number,
- The availability of cybersecurity experts is decreasing.
- While enterprise-level organizations are getting the proper cybersecurity solution,
- SMBs are struggling.
- While other MDR providers base their pricing on the technology and people they can replace,
- bluedog’s MDR pricing is based on the capabilities of those needing our service.
The bluedog Managed Detection and Response Service
- The most affordable and most complete MDR solution to date.
- Provides high-level of protection for the price of a standard solution.
- Includes Rogue Device Detection and Internal Vulnerability Scanning at no additional cost.
- Protects you 24/7/365 with our fully staffed SOC.
- We can be your whole cybersecurity team taking care of everything for you or work with your team.
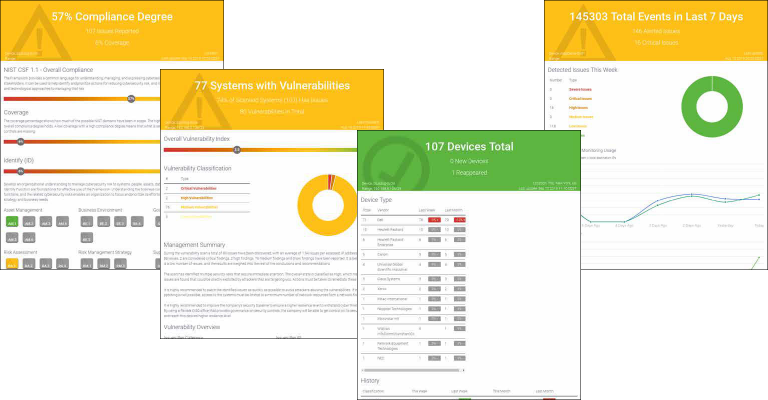
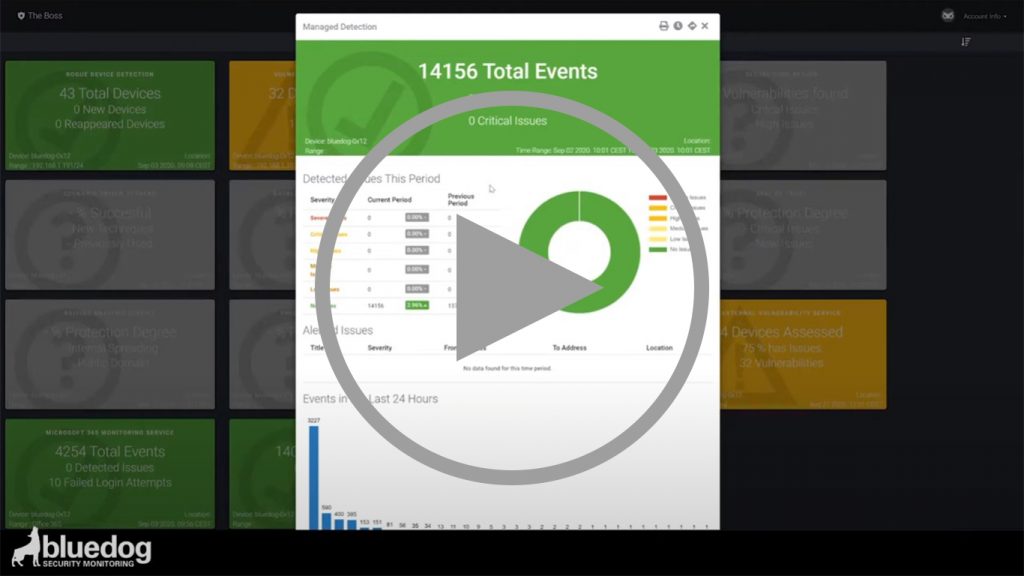
- Provides access to our dashboard giving full transparency of what is happening to your network as well as the devices connected to it.
- Our MDR Compliance Service can help you comply with your country’s cybersecurity compliance guidelines.
- Stores 365 days of data giving you details over time.
- Generates data from network activity as well as the devices connected to it ensuring that all data gathered is not tampered with.
See the following blog posts and Whitepaper for more information about MDR
Blog
Whitepapers
Managed Detection and Response Packages

MDR Essentials Rackmount A
- Includes all the key features
- Monitors up to 265 devices in 1 Subnet
- Monthly Subscription
- No Additional Hardware cost

MDR Essentials Rackmount B
- Includes all the key features
- Monitors up to 265 devices per Subnet Up to 3 Subnets
- Monthly Subscription
- No Additional Hardware cost

MDR Essentials Branch Office
- Includes all the key features
- Monitors up to 65 devices in 1 Subnet
- Monthly Subscription
- No Additional Hardware cost

MDR Compliance
- Can be added to any MDR Essentials Packages
- Includes our Management Dashboard for operational monitoring
- Includes Governance, Risk and Compliance (GRC) Monitoring
- Monthly Subscription
- No additional hardware cost